Introduction
Cybersecurity has become a critical concern for businesses, governments, and individuals. As technology advances, so do cybercriminals’ tactics, making traditional security methods less effective in protecting sensitive data and systems.
The old approach of “trust but verify” is no longer sufficient in a landscape where threats can come from inside and outside an organisation.
This is where Zero Trust Architecture (ZTA) comes into play. As a modern and proactive approach to cybersecurity, ZTA is designed to address the shortcomings of traditional security models by assuming that threats can be present anywhere, even within an organisation’s network.
In this blog, we’ll explore ZTA, why it’s necessary in today’s digital age, and how it can be implemented effectively to protect your organisation from ever-evolving cyber threats.
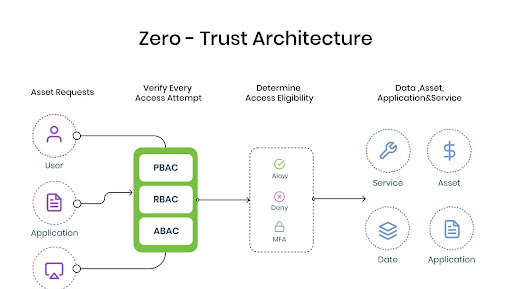
1. What is Zero Trust Architecture? A Simple Explanation
Source: Corsha
Zero Trust Architecture is a cybersecurity framework that operates on “never trust, always verify.” Unlike traditional security models that assume everything inside the network is safe, ZTA assumes that threats could be present anywhere, whether inside or outside the network.
This means that no user or device is trusted by default, regardless of whether they are within the organisation’s perimeter.
At the heart of Zero Trust is the idea that trust should never be granted implicitly. Instead, every request to access resources—whether from a user, device, or application—must be verified and validated before access is granted.
This continuous verification process helps to ensure that only authorised and legitimate activities are allowed.
For example, in a traditional security model, an employee working from the office might automatically be granted access to the company’s internal systems. However, in a Zero Trust model, the same employee must authenticate their identity and device security before being granted access, even if they’re working from the office. This ensures that even if an attacker gains access to the network, they would still be unable to access critical systems without further verification.
2. Why Traditional Cybersecurity Models Are Failing
Traditional cybersecurity models, often called perimeter-based security, are designed to protect the organisation’s network by creating a secure perimeter—like a castle with high walls. The idea is to keep threats out while trusting everything that’s inside.
However, this approach is increasingly ineffective in today’s digital landscape for several reasons.
First, the rise of remote work has blurred the boundaries of the traditional network perimeter. Employees now access company resources from various locations and devices, making it harder to maintain a secure perimeter.
Additionally, cloud computing has become integral to business operations, further complicating the concept of a fixed perimeter.
Second, cyber threats have evolved to become more sophisticated and persistent. Cybercriminals use advanced tactics like phishing, ransomware, and insider threats, which can easily bypass traditional security defences.
For example, a single compromised employee account can give an attacker access to the entire network, rendering perimeter defences useless.
Finally, the proliferation of mobile devices and the Internet of Things (IoT) has introduced countless new endpoints that must be secured. Each device connected to the network represents a potential entry point for attackers, making perimeter-based security models inadequate.
These challenges highlight the need for a new approach to cybersecurity—one that recognises the dynamic and complex nature of modern networks. Zero Trust Architecture addresses these challenges by shifting the focus from securing the perimeter to securing every interaction within the network.
3. Key Components of Zero Trust Architecture
Zero Trust Architecture is built on several key components that create a robust security framework. Here’s how these components help secure modern networks:
Identity Verification: Identity verification is the cornerstone of Zero Trust. Every user, device, and application must be verified before accessing any resource. This verification process often involves multi-factor authentication (MFA), which requires users to provide two or more forms of identification.
For example, users might need to enter a password and confirm their identity through a text message code or a biometric scan. Zero Trust significantly reduces the risk of unauthorised access by ensuring that only authenticated users can access resources.
Least Privilege Access: In a Zero Trust model, users are granted the minimum level of access they need to perform their tasks—nothing more. This principle of least privilege helps limit the potential damage a compromised account could cause. For instance, an employee in the marketing department would not have access to sensitive financial data, even if they are within the company network. By restricting access, Zero Trust reduces the attack surface and makes it harder for attackers to move laterally within the network.
Continuous Monitoring: Zero Trust requires constant network activity monitoring to detect and respond to threats in real-time. This means that even after a user or device is granted access, their actions are constantly monitored for any signs of suspicious behaviour. For example, if a user suddenly tries to access many sensitive files, the system might flag this activity as unusual and trigger an investigation. Continuous monitoring helps to quickly identify and mitigate potential threats before they can cause significant damage.
Micro-Segmentation: Micro-segmentation involves dividing the network into smaller, isolated segments, each with its security controls. This prevents attackers from moving freely within the network if they manage to breach one segment. For example, if an attacker gains access to a specific server, micro-segmentation ensures they cannot access other network parts without additional security checks. This approach dramatically reduces the risk of a widespread breach and contains potential threats to a limited area.
4. The Benefits of Adopting Zero Trust Architecture

Source: Rublon
Implementing Zero Trust Architecture offers several key benefits that make it an essential part of modern cybersecurity strategies:
Enhanced Security: Zero Trust significantly reduces the risk of data breaches and cyber-attacks by requiring verification for every access request and continuously monitoring network activity. Since no user or device is trusted by default, it becomes much harder for attackers to gain unauthorised access to critical systems. According to a report by IBM, the average cost of a data breach in 2022 was $4.35 million, making enhanced security through Zero Trust not just a necessity but also a cost-saving measure.
Flexibility for Modern Workplaces: Zero Trust is designed to support the flexibility needed in modern workplaces, where employees often work remotely and use various devices. Unlike traditional security models that rely on fixed perimeters, Zero Trust secures every interaction, regardless of where it originates. This makes it easier for organisations to support remote work and cloud services without compromising security.
Better Compliance: Data protection and privacy regulatory requirements are becoming increasingly stringent. Zero Trust helps organisations meet these requirements by providing a structured approach to security that includes identity verification, access control, and continuous monitoring. For example, the European Union’s General Data Protection Regulation (GDPR) mandates strict data protection measures. Zero Trust can help organisations comply with such regulations by ensuring that only authorised individuals can access sensitive data.
Reduced Attack Surface: By limiting access to resources based on need and implementing micro-segmentation, Zero Trust reduces the areas where attackers can infiltrate. This minimises the potential impact of a breach and makes it more difficult for attackers to move within the network. In essence, Zero Trust creates multiple layers of security, each acting as a barrier an attacker must overcome.
5. Implementing Zero Trust Architecture: A Step-by-Step Guide
Adopting Zero Trust Architecture requires careful planning and execution. Here’s a step-by-step guide to help you get started:
Assess Your Current Security Posture: Evaluating your cybersecurity setup before implementing Zero Trust is essential. Identify potential vulnerabilities, assess the effectiveness of your current security measures, and determine where Zero Trust principles can be most effectively applied. This assessment will help you understand the gaps in your security and prioritise areas for improvement.
Develop a Zero Trust Strategy: Once you’ve assessed your security posture, it’s time to develop a Zero Trust strategy that aligns with your organisation’s needs. This strategy should outline your goals, identify key focus areas (such as identity verification and access control), and establish a timeline for implementation. Consider involving stakeholders from different departments to ensure the strategy addresses the organisation’s needs.
Choose the Right Tools and Technologies: Implementing Zero Trust requires the right tools and technologies. Look for solutions that offer multi-factor authentication, continuous monitoring, micro-segmentation, and other essential Zero Trust features. For example, tools like Microsoft Azure Active Directory and Palo Alto Networks’ Prisma Access provide comprehensive Zero Trust capabilities that can help secure your network.
Educate and Train Employees: A successful Zero Trust implementation depends on the understanding and cooperation of your employees. Provide training to ensure that all staff members understand the principles of Zero Trust and their role in maintaining security. For example, employees should be familiar with multi-factor authentication processes and the importance of reporting suspicious activity. Regular training sessions and updates can keep security at the forefront of mind.
Continuous Review and Adaptation: Cyber threats constantly evolve, so your Zero Trust strategy should be, too. Regularly review and update your Zero Trust framework to address new vulnerabilities and incorporate the latest security technologies. For example, as your organisation adopts new tools or expands its operations, your Zero Trust policies should be adjusted to maintain robust security.
6. Challenges in Adopting Zero Trust Architecture
While Zero Trust offers significant benefits, implementing it is not without challenges:
Cost and Resources: Implementing Zero Trust requires substantial investment in new technologies, tools, and training. Smaller organisations may find the upfront costs challenging, especially if they need more resources to support ongoing maintenance and updates. However, it’s essential to consider the long-term benefits and potential cost savings from preventing data breaches and cyber-attacks.
Complexity and Integration: Integrating Zero Trust with existing systems can be complex, particularly for organisations with legacy infrastructure. Ensuring that all components—such as identity management, network segmentation, and continuous monitoring—work seamlessly together requires careful planning and expertise. Organisations may need to work with cybersecurity experts to ensure a smooth transition.
Cultural Resistance: Shifting to a Zero Trust model can be met with resistance from employees or stakeholders accustomed to traditional security models. Some may view the increased verification processes as cumbersome or unnecessary. To overcome this, it’s essential to communicate the benefits of Zero Trust clearly and provide training to help employees understand its importance.
Ongoing Management: Zero Trust is not a one-time implementation but an ongoing process that requires continuous management and adaptation. Organisations must allocate resources for regular monitoring, updates, and training to ensure their Zero Trust framework remains effective. This can be resource-intensive, but it’s essential for maintaining security in the face of evolving threats.
Conclusion
Zero Trust Architecture is more than just a buzzword; it’s a critical framework for protecting modern organisations from the ever-evolving landscape of cyber threats. As traditional security models become increasingly inadequate, Zero Trust offers a proactive and robust approach to safeguarding sensitive data and systems.
By shifting the focus from securing the perimeter to securing every interaction, Zero Trust reduces the risk of data breaches, supports modern workplace flexibility, and ensures compliance with regulatory requirements. While the journey to Zero Trust may present challenges, the benefits outweigh the costs.
If you’re concerned about your organisation’s security, now is the time to explore Zero-Trust Architecture.
By adopting Zero Trust principles, you can protect your organisation from today’s threats and prepare for tomorrow’s challenges. Don’t wait until it’s too late—start your Zero Trust journey today and take the first step towards a more secure future.





